The French government just launched its own messaging app called Tchap in order to protect conversations from hackers, private companies and foreign entities. But Elliot Alderson, also known as Baptiste Robert, immediately found a security flaw. He was able to create an account even though the service is supposed to be restricted to government officials.
Tchap wasn’t built from scratch. The DINSIC, France’s government agency in charge of all things digital, forked an open source project called Riot, which is based on an open source protocol called Matrix.
In a few words, Matrix is a messaging protocol that features end-to-end encryption. It competes with other protocols, such as the Signal Protocol that is widely used by consumer apps, such as WhatsApp, Signal, Messenger’s secret conversations and Google Allo’s incognito conversions — Messenger and Allo conversations aren’t end-to-end encrypted by default.
Riot is a Matrix client that works on desktop and mobile. You can join rooms, start private conversations, share photos and do everything you’d expect from a modern messaging app. Here’s what it looks like:
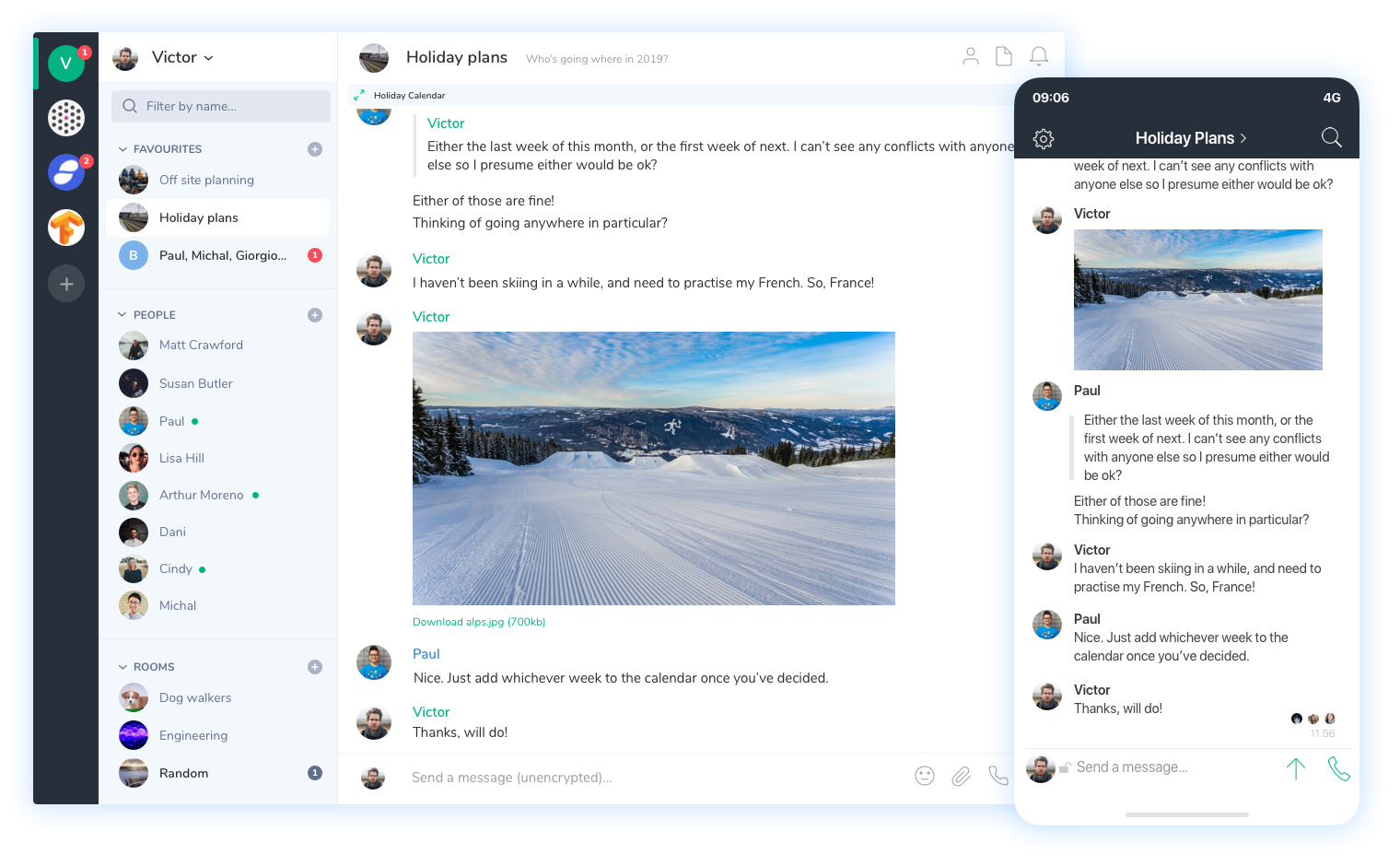
Developing Tchap became essential as Emmanuel Macron’s campaign team relied heavily on Telegram — the French government still uses Telegram and WhatsApp for many sensitive conversations. By default, Telegram doesn’t use end-to-end encryption. In other words, people working for Telegram could easily read Macron’s conversations. It’s a serious security weakness.
Similarly, you don’t want the Ministry of Defense to use Slack to talk about sensitive operations. The U.S. government could potentially issue a warrant to access those conversations on Slack’s servers.
Tchap features end-to-end encryption, and encrypted messages are stored on French servers. Access is restricted to government officials as you need to have an active email address that ends in @something.gouv.fr, or in @elysee.fr.
Yesterday, Alderson found out that you can create an account and access public channels even if you don’t have an official address. Adding @elysee.fr at the end of his email address was enough to receive the confirmation email to his real email address.
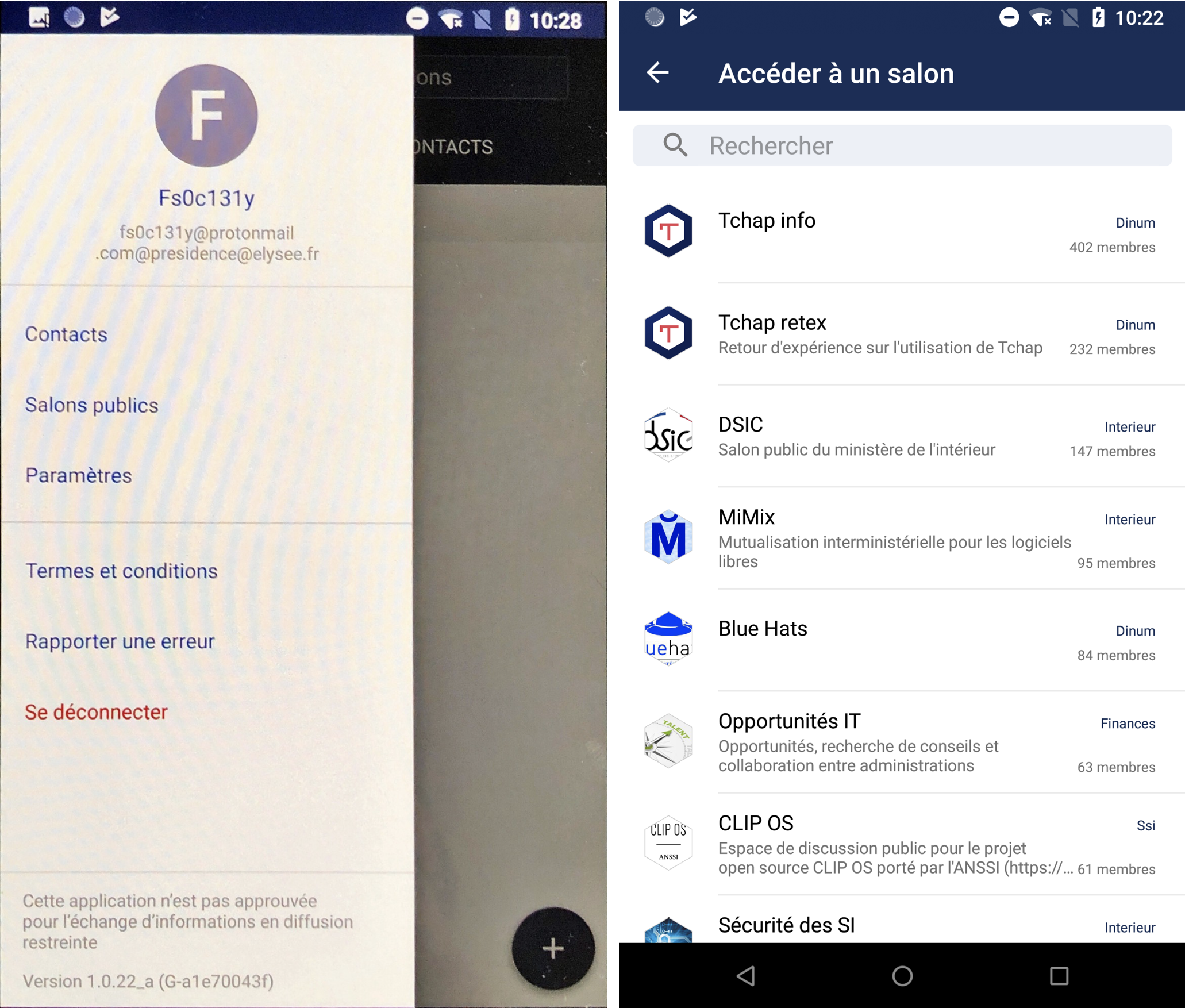
Alderson quickly disclosed the bug to the Matrix team. Matrix quickly issued a fix and deployed it. It was related to the identification system used by the French government.
We provided a fix which was deployed around 13:00 CET; the issue had not been exploited other than by @fs0c131y. We’re currently doublechecking for any instances of the same problem in other deployments.
— Matrix (@matrixdotorg) April 18, 2019
According to Alderson, there’s a bug in the parsing method used in a well-known Python module. The bug hasn’t been fixed since July 2018.
The good news is that Tchap is officially launching today. The DINSIC managed to fix this security flaw just in time before the official launch and somebody could leverage it. In its press release, the government says that the DINSIC will launch a bug bounty program to identify other vulnerabilities.