 Photo from Unsplash
Photo from UnsplashOriginally Posted On: https://www.alwaysvpn.com/guides/wireguard-vs-openvpn
When it comes to the latest and greatest VPN protocols, WireGuard might be seen as a fledgling name in the game, but how does it compare when up against the ever-reliable OpenVPN? It might seem like an obvious choice, but it’s not necessarily as cut and dried as you might have expected.
We put together a guide with everything you need to know about WireGuard and OpenVPN. You’ll see how each protocol compares in terms of speeds, security, and compatibility.
VPN Protocols Explained
Virtual private networks (VPN) use VPN protocols to create a stable and secure connection between your device(s) and the internet. A VPN protocol consists of specific rules or instructions that determine how data is routed to and from your device and the VPN server. It’s easy enough to use in practice, and you should be able to switch between any available protocols within your VPN settings menu. However, it’s not always obvious which protocol to choose.
There are many protocols designed for different circumstances. Some specialize in privacy while others help maximize connection speeds. Most VPNs offer multiple protocols you can choose from depending on what activity you’re doing. For example, if you plan to watch Netflix with a VPN, you may opt for a protocol that lacks some security measures but can help improve your internet speeds. This way you can enjoy your movie marathon without interruptions.
Two of the most popular and best protocols today include WireGuard and OpenVPN. We’ve detailed what to expect from both protocols in the following guide, but first, we’ll start with a brief introduction for each one.
What is WireGuard?
A reasonably new kid on the block, WireGuard is a VPN protocol created by Edge Security cryptographer, Jason A. Donenfeld. While many tests went out in 2019, WireGuard’s first stable release, or version 1.0.0., was on March 29, 2020.
In their own words, “WireGuard is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography. It aims to be faster, simpler, leaner, and more useful than IPsec, while avoiding the massive headache. It intends to be considerably more performant than OpenVPN.”
WireGuard was originally developed for Linux machines. However, it is now used for a variety of VPN apps on every major platform, remaining as open-source software that’s easy to modify. It’s designed to be a cleaner alternative to older protocols, with just 4,000 lines of code in comparison to the 70,000 found in the open-source version of OpenVPN. Modified versions of the latter also tend to be higher.
This lightweight protocol, therefore, uses less power than OpenVPN, is extremely user-friendly, and appears to be just as secure. It’s also much faster than OpenVPN. Don’t go jumping ship, though. There are plenty of areas OpenVPN excels in, too.
What is OpenVPN?
A more traditional protocol, OpenVPN was created and released back in 2001 by James Yonan–now the CTO of OpenVPN Inc.. It’s used to create secure point-to-point or site-to-site connections in routed or bridged configurations, most notably with client and server applications.
Like Wireguard, OpenVPN is also free, open-source software that’s available under the GNU license. OpenVPN works by using the OpenSSL library for encryption and authentication, and it can use either UDP (User Datagram Protocol) or TCP (Transmission Control Protocol) to transmit data from your device to a VPN server. Since its release, the OpenVPN software has been downloaded more than 50 million times, and nearly every VPN provider (worth considering) supports this protocol.
It might be slightly dated compared to newer protocols, but it’s a tried and tested method that’s undeniably the most popular option by a wide margin. Compared to WireGuard, it’s also more privacy-friendly and is supported by a greater number of VPNs today. How long this will remain true will depend on time.
For now, let’s compare each protocol side-by-side in terms of its speed performance, privacy/security, and compatibility.
Comparing SpeedsFor many users, there’s only one column that really matters – and that’s their speed. Connection speeds are incredibly important for any VPN, especially as data is being funneled to and from their servers before reaching your device. For the user, slower speeds mean more lag and buffering while waiting for services to load, with downloads definitely taking a lot longer.
As for VPN providers, it means an annoyed customer base and potentially a risk of lower profits when users begin to look elsewhere. It’s in everyone’s best interests to make the VPN as nimble as possible, and there’s an obvious winner when looking at the average connection speeds that can be achieved with WireGuard and OpenVPN.
The newer protocol wins easily.
An example of WireGuard’s performance can be found via its website. They provided some older benchmarks relating to speeds, which can be seen below:
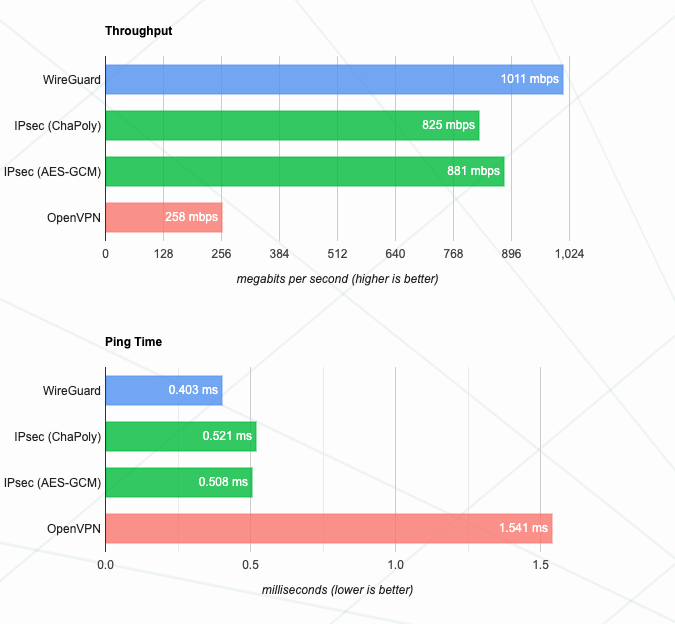 Source: WireGuard.com
Source: WireGuard.com
WireGuard notes:
“These benchmarks are old, crusty, and not super well conducted. In the intervening time, WireGuard and IPsec have both gotten faster, with WireGuard still edging out IPsec in some cases due to its multi-threading, while OpenVPN remains extremely slow. It is a work in progress to replace the below benchmarks with newer data.”
There was only ever going to be one winner, which makes sense as WireGuard creator Jason Donenfeld got the idea for the service in 2017 when in need of a “stealthy traffic tunneling solution” that could be used during penetration testing.
If you mainly use a VPN for streaming or gaming, switching to the WireGuard protocol while online could help you achieve faster connection speeds and reduce lag time. It’s definitely something to consider when shopping for a VPN provider.
Comparing Security & PrivacyIt’s a misconception to assume that WireGuard has worse encryption than OpenVPN just because it was built with speed in mind. What it does use is a simpler cryptography system, which does lead to less choice as a result.
On SecurityWireGuard deploys:
- ChaCha20 for symmetric encryption, authenticated with Poly1305
- Curve25519 for ECDH
- BLAKE2s for hashing and keyed hashing
- SipHash24 for hashtable keys
- HKDF for key derivation
Meanwhile, OpenVPN uses 256-bit OpenSSL encryption. It can use the AES, Camellia, 3DES, CAST-128, or Blowfish ciphers. It’s a reasonably robust selection and is superior to the fixed option given by WireGuard.
Performing well since its beginning, OpenVPN has been trusted to do the job for decades. Granted, even though WireGuard lacks the years of proof work that OpenVPN has, WireGuard does handle the security side effectively, too. It’s worth mentioning that there are currently no known security vulnerabilities for either WireGuard or OpenVPN.
On PrivacyIs there any real difference in terms of privacy between the two protocols? One major point of contention is that WireGuard configurations contain a static IP address. While OpenVPN might not have to log an IP, but WireGuard needs IP addresses to be stored on the server until it reboots. This is an obvious flaw, as an IP address can be matched with the user as a method of identifying them while online.
VPN providers tend to offer a solution to this problem in some shape or form.
For example, Mullvad advocates for the use of the WireGuard protocol with their VPN, but they acknowledge that keeping a static IP address for each device, even internally, is not ideal. Specifically, they note, “if a user experiences WebRTC leaks, that static internal IP address could leak externally. As another example, applications running on your device can find out your internal IP, and if you’ve installed software that is malicious, it can also leak that information.” Mullvad automatically replaces the WireGuard keys once a week, while you’ll be able to do so manually whenever you like within the app.
Meanwhile, IVPN apps regenerate a new key pair every 24 hours when using the WireGuard protocol. It also generates new IPs and distributes them to all servers automatically as well. You can see a breakdown of other ways this provider accounts for design issues intentionally used within the WireGuard protocol.
If you plan to use a WireGuard VPN, make sure to check if (and how) they’ve implemented any privacy-related workarounds. And for good measure, you can check it against the WireGuard whitepaper as well to verify that it makes sense for the protocol.
Overall, OpenVPN takes the lead in terms of privacy, while both protocols perform well from a security perspective.
Comparing CompatibilityA number of VPN providers have worked to adopt WireGuard as quickly as possible, hoping that the experimental protocol will provide a much-needed boost to speeds and performance. At the lower end, it can make a notable difference, but how does it perform in terms of compatibility?
Don’t be surprised if WireGuard isn’t supported by your favorite VPN, even if you’re using one of the bigger providers. For example, I’m currently testing the reasonably robust IPVanish, but they only offer WireGuard to beta users.
In comparison, they strongly advise using OpenVPN whenever it’s possible to do so.
The point is, you might find it difficult to get WireGuard working in the first place, even if you’re sold on what the protocol can do. Below, we recommend a few reputable VPNs that have implemented WireGuard in some shape or form over the past few years:
Private Internet Access (PIA)PIA scored highly in our recent review for its performance, network, and trustworthiness mainly. Another perk, though, is that their implementation of WireGuard is now available on all desktop clients and mobile applications.
They note that “Private Internet Access has augmented WireGuard with no logging privacy protections on your VPN servers, so PIA WireGuard users can rest assured that no client-server connections are logged and that their privacy is protected – as is and always will be standard at Private Internet Access.”
Visit Private Internet AccessRead our Private Internet Access Review
NordVPN
Rather than using WireGuard directly, NordVPN has taken a different tack. They created NordLynx, which is built around the protocol with a few differences. However, they do warn users to “please be aware that the WireGuard protocol is still under development. While we are confident in our implementation, WireGuard itself may still contain some unresolved bugs, so use it with caution.”
SurfSharkSurfshark rolled out WireGuard protocol support on Android, Windows, iOS, and macOS in October 2020. Another solid provider that we’d recommend checking out, they assign a dynamic IP address to all WireGuard users. So rather than using a static one, every time you connect to a VPN server using WireGuard, your IP address will be different.
CyberGhostThen there’s CyberGhost. An extremely competent VPN provider, their support pages confirm that WireGuard can be used on every major operating system, including mobile devices:
They’ve donated to the project directly. They also highlight WireGuard’s state-of-the-art cryptography as well as its ability to avoid anti-VPN systems that focus on OpenVPN connections.
ExpressVPNAnother solid VPN for WireGuard is ExpressVPN. It recently released Lightway, which is “a brand new, next-generation VPN protocol that will make your connection faster, more reliable, and more secure.” They continue by clarifying that “unlike the off-the-shelf protocols that most other VPN providers use, Lightway was built by ExpressVPN from the ground up to meet your needs, making it easier than ever to protect yourself online.”
It’s not the same as WireGuard, but they’d argue their custom-built tech is markedly better.
Other Types of VPN Protocols
In addition to OpenVPN and WireGuard, there are plenty of other security protocols VPNs offer. Each is catered towards specific online activities and is intended to personalize the user experience. We break down seven common VPN protocols below. Whether they’ll work for your setup is up to you.
Point–to–Point Tunneling Protocol (PPTP)The Point-to-Point Tunneling Protocol (PPTP) is essentially obsolete, having been around since the Windows ‘95 era. It’s still nippy and could be of use if you need faster connection speeds on older hardware. However, serious security vulnerabilities have been discovered while using PPTP, so it’s worthless from a security standpoint. PPTP uses MS-CHAP-v1 and MS-CHAP-v2 for authentication with both vulnerable to attacks. Google warned against the use of MS-CHAP-v2 back in 2012, noting that “an attacker who successfully exploited these cryptographic weaknesses could obtain user credentials. Those credentials could then be re-used to authenticate the attacker to network resources, and the attacker could take any action that the user could take on that network resource.”
Layer 2 Tunneling Protocol (L2TP)Released in 1999, the Layer 2 Tunneling Protocol (L2TP) was developed as a successor of sorts to PPTP. It’s typically used in conjunction with another VPN protocol, such as IPsec which is mentioned below. L2TP and IPsec are usually built into most operating systems as standard for this reason. The protocols are combined because L2TP doesn’t encrypt data on its own. It’s considered obsolete by some providers, including NordVPN, who no longer support the protocol as it “has a few convenient features, but certain issues prevent it from being a leading VPN protocol.”
Internet Protocol Security (IPsec)As we’ve mentioned, Internet Protocol Security (IPsec) is normally combined with other protocols to provide secure communications while online. It authenticates and encrypts the packets of data, and is available in either Transport mode or Tunnel mode. In Transport Mode, the IP addresses in the outer header are used to define the IPsec parameters that will be applied to the data packet. In comparison, Tunnel Mode is where two IP headers are sent to a server and the inner IP address defines the IPsec parameters need for the data packet. On the surface, IPsec appears to be relatively effective. However, it was named as an NSA weak point in the Edward Snowden documents published by The Intercept and Der Spiegel in 2014.
Secure Socket Tunneling Protocol (SSTP)SSTP (Secure Socket Tunneling Protocol) was developed by Microsoft, and introduced along with the release of Windows Vista. It’s seen as a more secure alternative to the likes of PPTP or L2TP/IPsec for Windows users, while it also works with macOS and Linux. One thing to note is that SSTP isn’t open-source, which could be a deal-breaker for some users. However, it does use TLS for security.
Secure Sockets Layer and Transport Layer Security (SSL/TLS)These VPN protocols go hand in hand. SSL was released in 1994 by Netscape Communications Corporation in an effort to secure their web sessions. However, a few years later TLS replaced SSL in 1999 due to security concerns. Transport Layer Security (TLS) is used to provide privacy and data security for communications over the internet, such as when loading web pages or sending emails. TLS is the most widely used security protocol on the net today. The stable TLS v1.0 release began development as SSL v3.1, which is why you’ll find that the two terms are often used interchangeably.
Internet Key Exchange Version Two (IKEv2/IPsec)Another widely used solution comes in the form of IKEv2/IPsec. The IKEv2 acronym stands for Internet Key Exchange, and IPsec is the Internet Protocol Security suite discussed above. Together, they combine to create a protocol that is used to enhance both speed and privacy. It’s widely implemented by VPN services as it requires less processing power, which helps with overall performance. This makes it an especially ideal mobile solution where users are quick to exit a page if load times exceed 2 seconds.
SoftEtherSoftEther is a more recent release, developed as thesis research by Daiyuu Nobori at the University of Tsukuba in Japan. They claim that the protocol offers a number of improvements compared to OpenVPN – which in itself is a tall order. SoftEther is currently available on Windows, Linux, macOS, FreeBSD, and Solaris, and the project is open-source and free to download. They note that “SoftEther VPN is the world’s only VPN software that supports SSL-VPN, OpenVPN, L2TP, EtherIP, L2TPv3, and IPsec, as a single VPN software.”
Which is Best?It’s easy to think of OpenVPN as a wheezy old man, especially when compared to an up-and-coming protocol that is now favored by many industry experts. However, WireGuard is still somewhat experimental, and it isn’t as widely available just yet.
Asking which one is better isn’t really the way to look at it, though. Instead, consider your user needs. Is speed of utmost importance to you? Or, do you care most about privacy or device compatibility? Figuring out your specific VPN needs first will help guide your decision. Either protocol is solid from a privacy and security perspective, although WireGuard falls behind in terms of compatibility. It’s to be expected, and the scale should be balanced more evenly in the future as it becomes more widely adopted.
Overall, you’ll be able to boost your online privacy drastically with the use of a fully audited VPN service. For OpenVPN, we recommend testing out Private Internet Access. Whereas NordVPN might be more ideal if you want to learn the ins and outs of WireGuard on a range of devices. It ultimately comes down to preference.